- Nov 21, 2017 A new display engine allows Reflector 3 to display the edge-to-edge iPhone X screen with a frame. Screenshots Instantly take full-resolution screenshots of any connected device. Windows-Specific Upgrades On Windows, Reflector 3 is located near the Start button instead of the system tray by the clock where Reflector 2 was located.
- Reflector 3 is one of the most popular mirroring applications for Android and iOS users. It offers different functions which are deemed useful. For example, you can stream your mobile devices simultaneously on your Windows and Mac PC. Furthermore, one can capture their screen performance and add narration or audio if needed.
“Reflector 3 is a wireless mirroring and streaming receiver that works with Google Cast and Airplay-enabled devices. Everything you do on your phone, tablet or computer can be wirelessly sent to Reflector.” (Reflector website). Www.Reflector.com 1150 Sugg Pkwy Greenville, NC 27834 Main Phone: 252-329-9500 Customer Care Phone: 252-329-9505. Services About Us; Contact Us; Subscription Portal; Password Reset.
[ Read my product review disclosure statement here. ]
As I was researching my upcoming webinar on VR, I needed to find a way to stream my iPhone screen, because there’s an application that controls the VR camera that only runs on iOS.
Creating a still image of the iPhone screen is easy: press two of the side buttons; which two depends upon which version of iPhone you have. But showing an iOS screen live? Hmmm… that requires different software.
After some research, I discovered Reflector 3, by Squirrels.
NOTE: I first wrote this review using the trial version. Then, when I realized that I really needed this software for my upcoming webinar, I bought it and replaced all my screen shots.
EXECUTIVE SUMMARY

“Reflector 3 is a wireless mirroring and streaming receiver that works with Google Cast and Airplay-enabled devices. Everything you do on your phone, tablet or computer can be wirelessly sent to Reflector.” (Reflector website)
While this software works great for streaming, it is actually part of a much larger set of software specifically designed for education, where a teacher can monitor what students are doing on their mobile devices, including: accessing and managing preferences, customizing student devices, recording device screens, connecting Chromebooks, Android devices, iPads and iPhones and checking on student work.
Manufacturer: Squirrels
Website:https://www.airsquirrels.com/reflector
Price: $14.99 (US)
Squirrels provides a full-function 15-day free trial, which watermarks the image.
GET STARTED
Both the iPhone and the computer need to be on the same network. Once they are, start Reflector 3 on your computer.
(This screen only appears when you are running the trial version of Reflector 3.)
On the iPhone or iPad, swipe to reveal the Control Center.
Tap Screen Mirroring
Tap the name of your computer. The software displays a code on your computer which you enter into your iOS device.
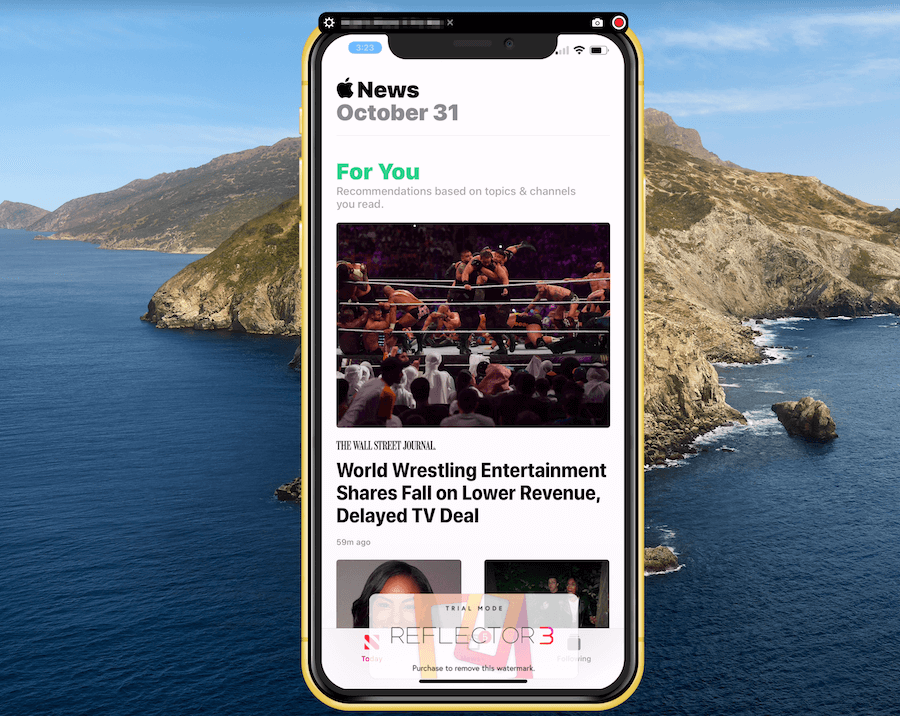
Once the code is accepted, your iOS device is mirrored on your computer desktop. This is perfect for live streaming from a phone. The actual image is quite large, filling most of the vertical space on the screen.
RECORDING THE SCREEN
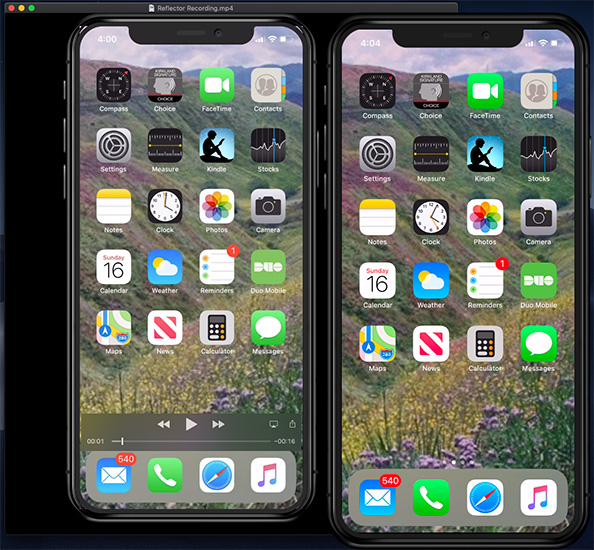
While I record my webinars using ScreenFlow, from Telestream, sometimes you may need to record just the iPhone screen by itself. By clicking the red record button in the top right corner of the iPhone image on your computer, you can record the iPhone on your computer. This generates an MP4 video file which can be stored on your desktop. This is an ideal screen-capture utility because it uses the storage capacity of your computer, rather than your phone.
NOTE: Once you end recording, Reflection 3 requires time to convert the file and save it. I found that, on my system, this takes about real time to export.
Also, the camera icon, just to the left of the red record button, allows you to capture a screen shot directly to your computer, which greatly simplifies moving screen shots from an iPhone to a computer for articles such as this.
Here’s the iPhone movie on the left, with the live stream overlaid on the right. (The trial version is watermarked.) The MP4 file can be edited in the NLE of your choice. The image size is big – 1792 x 1792 pixels – so you have plenty of resolution to work with.
OTHER OPTIONS
There’s also a menu bar utility that displays all the devices connected to your computer via Reflection 3, while the gear menu allows access to preferences, software updates, and other options.
SUMMARY
Squirrels has a variety of software tools that allow different devices to connect and stream wirelessly. While I haven’t used Reflection 3 in one of my weekly webinars, that will change starting with this Thursday’s presentation.
So far, I’m very impressed with how easy Reflector 3 is to use and how well it works. The actual screen quality is excellent. I’m looking forward to using it in the future.
EXTRA CREDIT
Here’s a link to learn more about their educational versions: Reflector Teacher.
Bookmark the permalink.In most world class companies there is an increasing pressure to protect computer networks against unauthorized intrusion, engineering systems are the major concerns of administrators. Their aspiration is to create a robust system that can withstand attack. However, no man made system can be made impenetrable. Our Data Analysis for Network Cyber-Security solutions focuses on monitoring and analyzing network traffic data, with the intention of preventing, or quickly identifying, malicious activity.
Such work involves the intersection of statistics, data mining and computer science. Fundamentally, network traffic is relational, embodying a link between devices. As such, graph analysis approaches are a natural candidate. However, such methods do not scale well to the demands of real problems, and the critical aspect of the timing of communications events is not accounted for in these approaches.
This book gathers papers from leading researchers to provide both background to the problems and a description of cutting-edge methodology. The contributors are from diverse institutions and areas of expertise and were brought together at a workshop held at the University of Bristol in March 2013 to address the issues of network cyber security. The workshop was supported by the Heilbronn Institute for Mathematical Research.
Security and operations teams are inundated with change requests – many of which are still handled manually. In the rush to meet Service Level Agreements, engineers are sometimes forced to compromise security or compliance.
With Desiderata, network engineers can say goodbye to compromising security in the name of expediency. Change management solutions give organizations the awareness and tools they need to securely open and revise access.
Real-time security analysis – Gauge the efficacy of your existing firewall policies, including comparative scoring, to understand current access enforcement.
Policy search – Quickly search all devices within the enterprise domain from a single place in the application
Traffic flow analysis – Trace the source and destination of every rule in each of your existing firewall policies (including NAT) to understand traffic flow.
What We Do
We offer a variety of services to our clients including

Training
Data Center Engineering and Management
Network and System Engineering
Website and Security Analytics
Using expert tools to focus network security and risk analysis enables you to:
- Measure overall network risk posture.
- Allocate pentesting resources.
- Rapidly mitigate vulnerabilities.
Potential Attack Visualization
Reflector 3 Reviews
Access Path Analysis
Where is your network at risk?
Desiderata’s network security and risk analysis feature provides detailed visibility into access controls and exposes vulnerabilities in the network. Our tools filters vulnerability scanner results, simulates potential attack paths and uses host and data values to provide clear and precise remediation steps and reduce overall exposure to access-based risk.
14
Reflector 3 Download For Mac
1200
+
100
%
Our Location
The very first place to turn to for informative article help is your high school or school library.